Virtual Private Networks
Some facts
- Your ISP can see every website you visit, notably due to name resolution requests.
- HTTPS, or HTTP over SSL has now become a standard. Thus the content (this is important) of your requests are mostly encrypted, but not necessarily its routing (think mail, the postman can see the sender and recipient addresses on the enveloppe but not the content of the enveloppe).
- Despite this content encryption your activity still can be (i.e.: is) tracked and monitored through the use of technologies such as cookies, pixel trackers, your web browser, extensions,...
- IP addresses (the network endpoints identifiers) batches are allocated geographically, and one can pinpoint the rough physical location of an IP using publically available GeoIP databases.
What can a VPN do?
- Bypass censorship, e.g. accessing websites otherwise blocked by local ISP
- Spoof your location, e.g. use a VPN server located in another country as a public facing IP to access website that filters traffic based on location
- Encrypt data between you and the VPN server
The last one is interesting as a VPN does encrypt DNS requests, effectively masking endpoint routing from middlemen (e.g.: ISPs). The ISP then only sees you are accessing the VPN server's IP, but not the requested ressource's one. This is achieved via encapsulation of TCP or UDP packets depending of the chosen tunneling protocol implementation.
Keep in mind that the VPN server is the breakpoint of the encryption. In a VPN secured tunnel, communication is only encrypted between the VPN client application and the VPN server. Everything that goes out from the VPN server won't necessarly be, and the VPN server's IP address will be visible by the destination server.
What a VPN cannot do
- Protect you from viruses or malwares
- Hide everything you do on the internet
- Connect to a distant network without an ISP
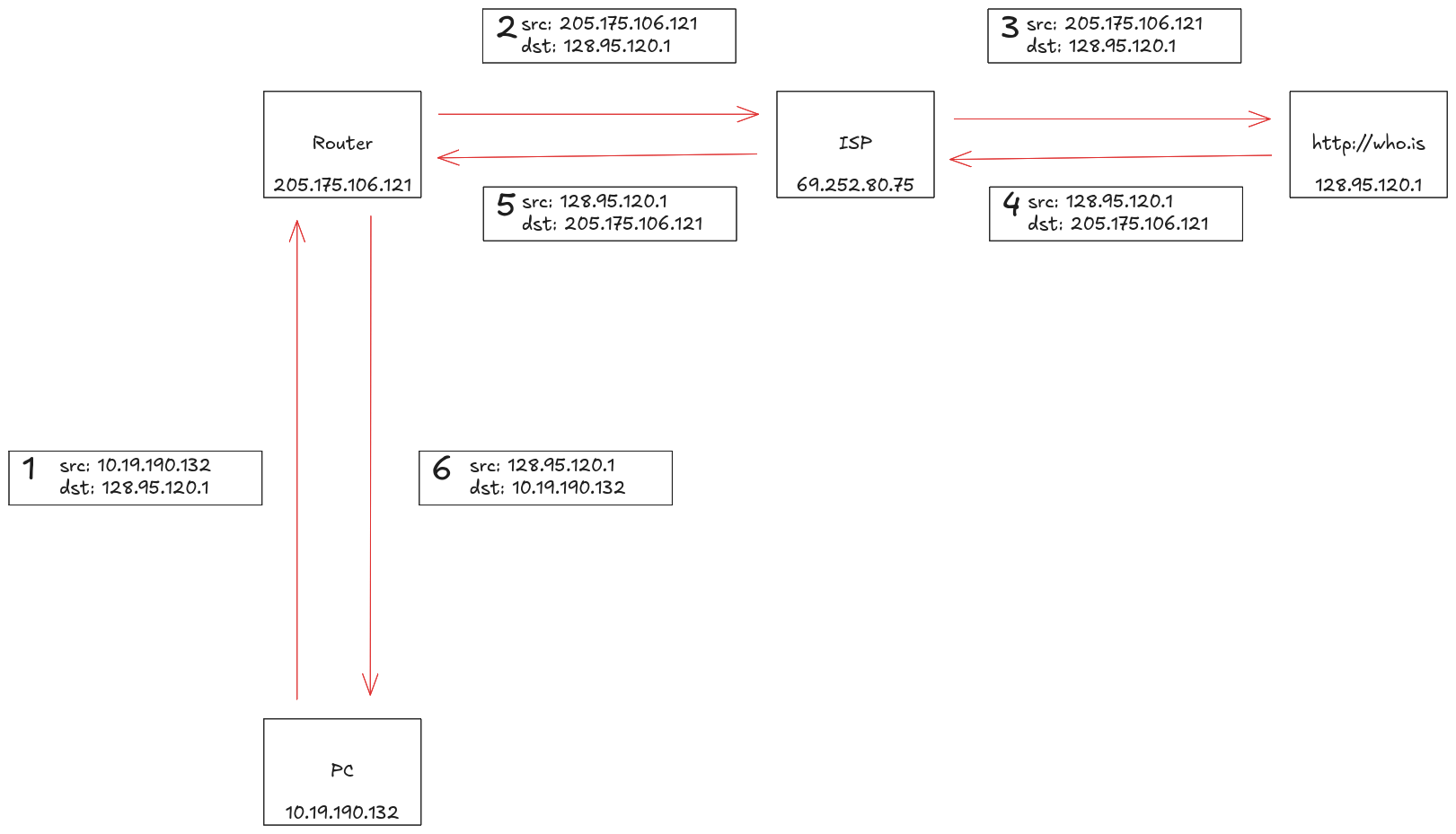 |
|---|
| Here without a VPN |
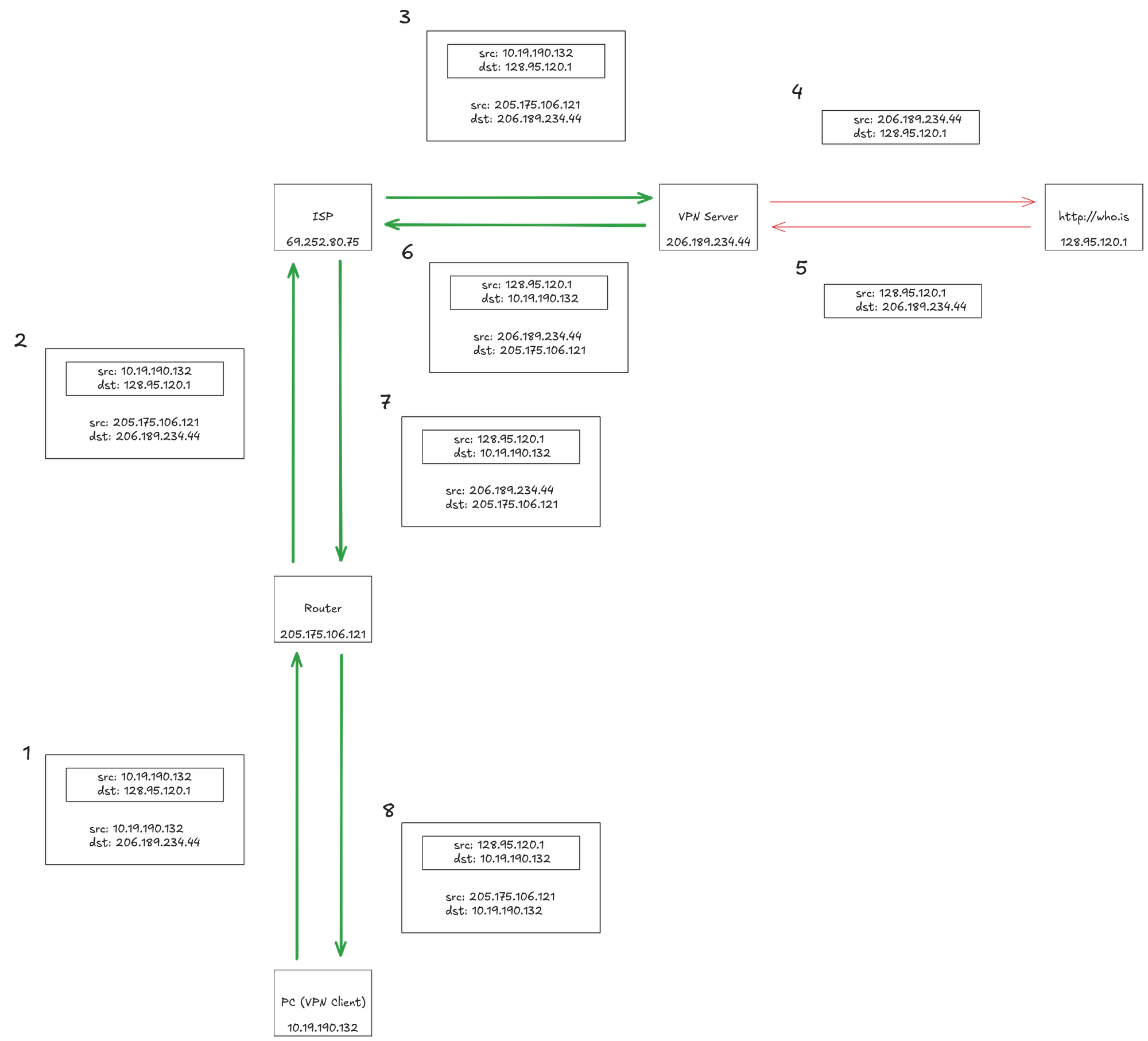 |
|---|
| Here with a VPN |
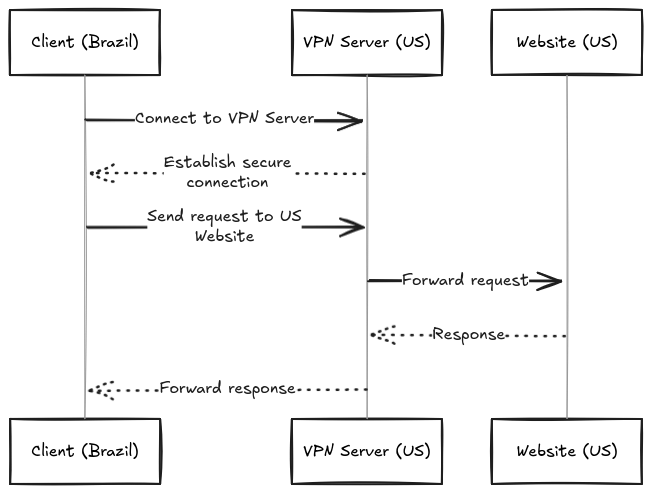 |
|---|
| A Brazil based client can access US ressources as if he had a US IP address |
A note on proxies
A proxy acts as an additional hop between you and the server you're trying to reach. Depending on the proxy's configuration, one can effectively masquerade its IP address and achieve location spoofing just as well as a VPN. Note that, unless VPN, proxies does not encrypt DNS requests and the packets routing fields will be visible by the destination server and every router along the packets route. Although, one can configure the proxy server to remove the content of the X-Forwarded-For header on the forwarded requests, thus hiding their primary origin IP.
Why self host?
One can get a VPN server using a private service provider such as NordVPN, Surfshark, Proton, and the likes. This can be convenient for some, but the convenience comes at the price of trust. One has to put a lot of trust on the service provider logging and data privacy policies, which can be prohibitive for some.
Self hosting your own VPN server on the other hand ensures you have complete control over its logs and configuration, as well as data securization, which can be interesting for sensitive use cases.
Wireguard
Wireguard is a rather recent tunneling communication protocol for encrypted virtual private networks, leveraging asymetric public-key cryptography. It aims at being simpler, lighter, and faster than bloated old industry standards such as OpenVPN or IPsec. Wireguard passes traffic exclusively via the stateless UDP protocol. This is a limitation to keep in mind when implementing a VPN solution as it can cause issues like gateways automatically closing connections if keepalive aren't properly configured.
Its default port is UDP 51820
Wireguard is also conveniently the name of a program implementing the eponymous protocol.
Why docker?
For convenience as well as fine tuning and reproducibility of environment.
How?
On an ideally located server, one can install a docker daemon and use it to run a Wireguard container. The following docker-compose can be used as a starting point:
services:
wireguard:
image: linuxserver/wireguard
container_name: wireguard
cap_add:
- NET_ADMIN
- SYS_MODULE
environment:
- PUID=1000
- PGID=1000
- TZ=<your-timezone>
- SERVERURL=<your-server-url> #optional
- SERVERPORT=51820 #optional
- PEERS=1 #optional
- PEERDNS=auto #optional
- INTERNAL_SUBNET=10.13.13.0 #optional
volumes:
- /opt/wireguard-server/config:/config
- /lib/modules:/lib/modules
ports:
- 51820:51820/udp
sysctls:
- net.ipv4.conf.all.src_valid_mark=1
restart: unless-stopped
Note that this docker compose is Linux oriented and will bind the /opt/wireguard-server/config and /lib/modules local directories. This can obviously be tweaked to get a local install in a single directory for instance.
See image documentation for more information.
For practicality, one should install the Wireguard client application directly on the client, without any containerization.